In a nutshell… The SharePoint Audience feature is not security… ever. Audiences are used to filter (hide), not secure.
Some may consider the use of Audiences as “security by obscurity”, but it is not security.
From my SharePoint Security book… (on Amazon – 2013/2016 version coming soon.)
Audiences
SharePoint audiences are used to target content to specific groups of people by hiding it from those who don’t need to see it. These groups can be SharePoint groups, Active Directory security groups, Active Directory distribution lists and SharePoint global audiences that are based on user profile data.
Audience targeting can be used with:
- List and library items, but only when displayed using a Content Query Web Part (part of the Publishing feature).
- Entire web parts.
- Top Link and Quick Launch navigation links. (when Publishing features are enabled)
Note: The Audiences feature is only available with SharePoint Server Standard and Enterprise editions. SharePoint Foundation has no support for Audiences. (Audiences is part of User Profile Services.)
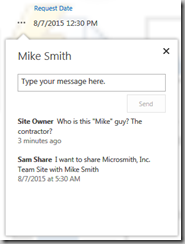
Audiences are not security!
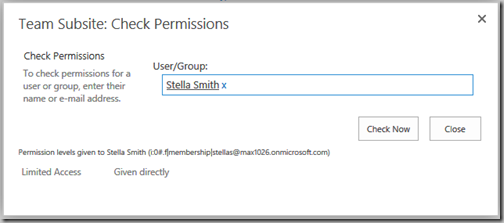
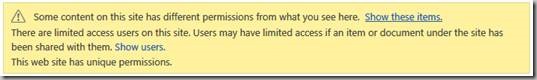
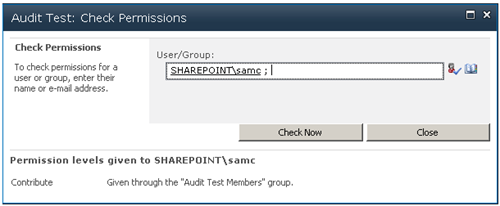
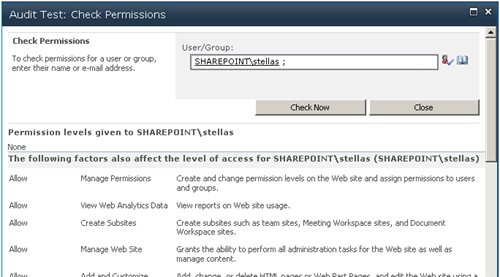
Audiences are usually described as being used to "target" content to a selected group. Audiences could also be described as being used to hide content from all users except for the target audiences. This second form sounds like security, but absolutely is not. While a list item or document web part might have a target audience, and non-audience members won't see the web part, if it is not otherwise secured they can still get to the item by using a direct URL or find it from search.
The Audience feature should be thought of as a filtering option, not security.
To filter list items using an Audience
List and library items can be filtered using the Audience feature using the Publishing feature’s Content Query Web Part. While the regular list web parts have an Audience feature, that feature hides the entire web part, not selected items. The Content Query Web Part is added to a site collection when you enable the Publishing features.
Four steps are required to filter list content using an Audience:
· Create a publishing site or enable the Publishing Infrastructure feature on a site collection.
· Enable the Audience feature on the list.
· “Tag” list items by Audience.
· Display the list using the Content Query Web Part.
Step 1: Enable the SharePoint Server Publishing Infrastructure Site Collection feature
First make sure there are no other reasons to not enable the Publishing features. (Policy, support, governance, etc.)
1. Go Settings (gear), Site Settings of the top level site of the site collection.
2. In the Site Collection Administration section click Site collection features.
3. If not already activated, activate the SharePoint Server Publishing Infrastructure feature.
Step 2: Enable the Audience feature on the list or library
1. Go the list or library, click the LIST or LIBRARY tab in the ribbon.
2. Click List Settings or Library Settings.
3. Click Audience targeting settings.
4. Checkmark Enable audience targeting.
A new field named Target Audiences will now be displayed in the New and Edit pages for the list.
5. Click OK.
Step 3: “Tag” list items by Audience
1. Edit the properties of a list or library item.
2. In the Audience area click the Browse button ( ) and select an Audience.
3. Save the changes to the item.
Step 4: Display the list using the Content Query Web Part
1. Move to your page where you want to display the web part.
2. Edit the page.
3. Click the Insert ribbon tab and the Web Part button.
4. Click on the Content Rollup category and then click the Content Query web part. (If the web part is not listed then you do not have the SharePoint Server Publishing Infrastructure site collection Feature enabled.)
5. Click Add to add the web part to the page.
6. Click the web part’s dropdown menu and click Edit Web Part.
7. Expand the Query section.
8. Select the Source (the scope) for the rollup from one of the following: Show items from all sites in this site collection, Show items from the following site and all subsites, or Show items from the following list.
9. Select the List Type and the Content Type to select the content to display from the Source selected above.
10. In the Audience Targeting section checkmark Apply audience filtering.
11. Optionally add filters or Presentation options.
12. Click OK to save your web part changes.
13. Save the page and test the results.
Note: the Target Audience option in the Advanced section of the web part’s property panel is used to control if the entire web part will be displayed for an audience.
Search Web Parts vs the CQWP
Microsoft currently recommends using the Search Web Parts in many of the places that we might have used the CQWP. While search uses cached content, and can be quite a bit faster, the data is only as current as the last search crawl. (I.e. Completed tasks may still display as incomplete.) The CQWP is always using live data and can be Audience filtered.
Resources for the CQWP:
Display data from multiple lists with the Content Query Web Part:
https://support.office.com/en-US/article/Display-a-dynamic-view-of-content-on-a-page-by-adding-the-Content-Query-Web-Part-3e35bd58-d159-43d6-bfc7-77878b4a856d (or just do a web search for “Display a dynamic view of content on a page by adding the Content Query Web Part”)
To show web parts for an Audience
You can use Audiences to hide an entire web part from all users except for the selected audiences. Simply edit the web part, expand the Advanced section and select an audience.
Note: The SharePoint Server Publishing Infrastructure Site Collection feature is not needed for web part Audience filtering.
To display a Quick Launch or Top Link Bar link for an Audience
Links in the Quick Launch and the Top Link Bar can be filtered by Audience when the Publishing Infrastructure feature has been activated. Once this feature has been activated the Quick Launch and Top Link Bar options are replaced with a single Site Settings option named Navigation. In the Navigation page Quick Launch is called Current Navigation and the Top Link Bar is called Global Navigation.
Enable the SharePoint Server Publishing Infrastructure Site Collection feature:
1. Go Settings (gear), Site Settings of the top level site of the site collection.
2. In the Site Collection Administration section click Site collection features.
3. If not already activated, activate the SharePoint Server Publishing Infrastructure feature.
To filter navigation links:
1. Go Settings (gear), Site Settings.
2. In the Look and Feel section click Navigation.
3. Scroll down to the Navigation Editing and Sorting section of the page.
4. Add or edit a Heading or a Link.
5. In the Audience area click the Browse button ( ) and select an Audience.
6. Set the Title, URL and other options as desired and click OK.
7. Test! The new navigation item should only be displayed for the selected Audiences.