Note: The following is for SharePoint 2010 Beta 2 and does not work in the RC or RTM releases. So this was an interesting exercise, but has no future value…
While searching the web to see if anything had changed with SharePoint 2010 authentication and how to setup Forms Based Authentication (FBA) all I was finding was how to setup up FBA using the new Claims Based approach. While interesting, I was just looking to accomplish what we have been doing all along in SharePoint 2007; create an application using Windows Authentication and then “Extend” it to create a second IIS application based on FBA. Since I didn’t find what I was looking for, I went through all of the steps to basically do what we did in 2007, and found only a few differences.
First of all… if you have done this for SP 2007, then you already know most of the steps…
Setting up SharePoint 2010 for Forms Based Authentication
Overview:
- Create a store for the user data (I’m using the ASP.Net default tables)
- Create a Windows Authenticated application and a top level site.
- Extend the application.
- Edit the web.config of the extended application, and the web.config of Central Administration.
- Add users
- Test…
What has changed with2010?
- You can do FBA with Claims Based authentication (but that’s not what I was looking for here)
- With Claims Based you can do multiple types of authentication in a single application – no need to extend. (but you will then have only one IIS application and a single web.config. You may other reasons to want these to be separate.)
- All of the screens in Central Administration ;-)
- Almost nothing else… (including the lack any FBA user maintenance screens)
Run ASPNET_REGSQL.exe to build the SQL tables for the user data.
You need to store your user names, passwords, etc somewhere. If you can created your own custom membership provider then you can store your data anywhere you like. If you are using the out of the box .Net membership provider then you can use one of the .Net tools to create the database and tables.
- Open a command prompt and navigate to the C:\windows\Microsoft.NET\Framework\v2.0.xxx directories or better if you have Visual Studio 20xx installed, go to Start, All Programs, Microsoft Visual Studio 20xx, Visual Studio Tools and Visual Studio Command Prompt (it already knows the path to the .Net tools).
- You could type ASPNET_REGSQL and press enter to run the wizard, but it create tables for features you are not using. Instead, supply the command prompt options.
C:\> aspnet_regsql -S localhost\sharepoint -d aspnetdb -E -A m
Start adding the following features:
Membership
....
Finished.
This example uses
Windows authentication: –E
a SQL Server: -S localhost\sharepoint
to create a database named: -d aspnetdb
and in that database create the membership tables: -A m
Type aspnet_regsql /? for all options. - If you are curious, launch your SQL tools and browse the database and tables just created.
Create the initial application:
For testing purposes you may want to create a new SharePoint Application and Site Collection from Central Administration.
- This application will be created as an ordinary SharePoint application with Windows authentication (Classic Mode Authentication). Do not enable anonymous.
- The initial site owner for the site collection should be a Windows authenticated user (an administrator account will do for a test)
To extend or not extend?
You could just follow the steps below to change the application’s authentication from Windows to Forms, but Windows authenticated users, such as Search, would not be able to access the site! As an alternative you can Extend the SharePoint application by creating new IIS application that shares the SharePoint’s databases with the Windows authenticated application. This will create a new IIS application, a new folder (typically in INETPUB) and a new web.config. The last is the most important as the web.config is where we configure FBA.
To Extend an application:
- Go to Central Administration, click Application Management and click your existing application. (In my example, SharePoint – 83)
- Click the Extend button in the Ribbon.
- Enter a name, and if needed, a port number or host header (If this is for an internet facing application then you will probably use port 80 and a host header)
- Click Yes under Allow Anonymous. (This does not allow anonymous access to sites, pages or lists yet, that has to be enabled in the sites. This can also be done later.)
- Note that for authentication you can only choose Negotiate (Kerberos) or NTLM, not FBA. You will do this later.
- Pick a Zone. Note the Default is missing from the list. (The actual zone choice is not important as they could have just been called Zone 1, Zone 2, etc.)
- When you click OK the new application will be created. You can see that they are both sharing the same SharePoint databases by navigating to both of the application URLs. In my case:
http://maxsp2010beta2:83/SitePages/Home.aspx
http://maxsp2010beta2:84/SitePages/Home.aspx
The only difference between the two so far are the port numbers and the second allows anonymous access.
Note that this extended application is not listed with the other applications in Central Administration as it an alternate access to an existing application, not a standalone application. In the screen below you just see “SharePoint – 83”.
You can see both applications in IIS. To see the extended application in SharePoint select “Authentication Providers” in the Ribbon:
The extended application is the “Internet” Zone. (The zone you picked) - Click your zone (Internet in this example)
You will return here later to configure Forms authentication, but first you need to configure a Membership provider in the web.config of the extended application and create a database to store your user tables.
- Enter a name, and if needed, a port number or host header (If this is for an internet facing application then you will probably use port 80 and a host header)
Now update the extended application’s web.config
You need to define a membership provider. The steps here show you how to copy one from the machine.config.file.
Make sure you are editing the Extended application’s web.config! In my example it would be SharePoint – 84, not SharePoint – 83.
- Open the web.config in your favorite XML editor (Notepad, Visual Studio, etc)
- Open the machine.config file to do some copy and paste work
C:\Windows\Microsoft.NET\Framework\v2.0.50727\CONFIG\machine.config
(Why not the configs in 4.0? SharePoint 2010 is a 3.5 application and 3.5 is built on top of 2.0) - Microsoft added default entries for the membership provider and for a SQL connection string in machine.config. You copy and edit these for your own use. Find the <membership> section, copy it and paste it into your application’s <system.web> section.
Two changes: I used a new name for the provider: MyAspNetSqlMembershipProvider and I set a default provider using the new name.<system.web> <membership defaultProvider="MyAspNetSqlMembershipProvider"> <providers> <clear /> <add name="MyAspNetSqlMembershipProvider" type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="aspnetdb" enablePasswordRetrieval="false" enablePasswordReset="true" requiresQuestionAndAnswer="true" applicationName="/" requiresUniqueEmail="false" passwordFormat="Hashed" maxInvalidPasswordAttempts="5" minRequiredPasswordLength="7" minRequiredNonalphanumericCharacters="1" passwordAttemptWindow="10" passwordStrengthRegularExpression="" /> </providers> </membership>
<roleManager enabled="true"> <providers> <add name="MyAspNetSqlRoleProvider" connectionStringName="aspnetdb" applicationName="/" type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" /> </providers> </roleManager>
See here for more info: http://msdn.microsoft.com/en-us/library/system.web.security.membership.aspx
(Notice that there is no mention of SharePoint there. This is a .Net feature.)See here for details on the properties: http://msdn.microsoft.com/en-us/library/system.web.security.membership_members.aspx
- Note the connectionStringProperty described above. LocalSqlServer is also defined in machine.config and needs to be changed or overwritten as the default points to a SQL Express database, and you created your own database and tables above. I changed it the machine.config’s LocalSqlServer to my own aspnetdb and added a <connectionStrings> section to the application’s web.config.
Note that this the connection string to your database.
<connectionStrings>
<add name="aspnetdb"
connectionString="Data Source=MAXSP2010Beta2\sharepoint;Initial Catalog=aspnetdb;Integrated Security=True"
providerName="System.Data.SqlClient" />
</connectionStrings>
Note: the Role manager is optional, but if you what the equivalent to Windows Groups then also add the Role manager to the web.config. - Now find this following line and edit it (or copy and paste it back as a new line) using your membership provider’s name:
Copy:<add key="AspNetSqlMembershipProvider" value="%" />
and paste back as:
<add key="MyAspNetSqlMembershipProvider" value="%" /> - Save the config file.
- Display the site from both the original and the extended URLs and make sure you have not broken anything while editing the web.config.
Turn on FBA and tell SharePoint to use your membership provider…
- Return to Central Administration and in the Application Management section click your SharePoint application.
Click “Authentication Providers” in the Ribbon:
The extended application is the zone you picked. - Click your zone (Internet in this example)
- In the Authentication section click Forms.
Notice that the form is redrawn with new options and that “Client Integration” has been disabled. Microsoft Office prior to Office 2007 SP2 did not “play nice” with SharePoint when using FBA. (Office did not understand cookies prior to SP2) - Enter the name of your Membership provider exactly as it is listed in your web.config.
Note: the Role manager is optional, but if you what the equivalent to Windows Groups then also add the Role manager to the web.config and to this page. - Click Save
Central Admin just changed your web.config (as it often does).
This was the authentication section for Windows before turning on FBA:
<authentication mode="Windows" />
and here is the after:
<authentication mode="Forms">
<forms loginUrl="/_layouts/login.aspx" />
</authentication>
Now you have a SharePoint application with two “Doors”. One door is secured using Windows authentication and the other by forms with data stored in SQL Server (or where ever your Membership provides stores user data)
You are not done yet!
Your initial application still works for Windows authenticated users, but the second now has a locked door! If you visit the site with the extended URL you will just get a login form. Now you know why it is called “Forms” based authentication. And you can also now see why anonymous was needed… so users can visit at least one page unauthenticated, this form, so they can login.
So what have we done so far…
- Created a database in SQL Server to work with the default .Net membership provider to store user login data.
- Created an application that uses Windows authentication so we can do inside the firewall administration and so other tools, like Search, can access the site.
- Extended this application so we can have to web.config files (among other things) to configure Anonymous access, Membership providers and other things.
- Enabled FBA
Add your first FBA user
You now need to add a user for your site. While SharePoint did provide a login page (/_layouts/login.aspx) it does not provide FBA user administration fools. You can look to sources like codeplex.com or write your own. (The current FBA codeplex project is for 2007 and does not work “as-is” in 2010. You can down load it and change the references to 2010 and it does work.)
IIS 7.0 does have limited tools to add FBA users. Visual Studio also has Web Site manager that can be used to add users.
- Launch IIS: Start, Administration Tools, Internet Information Services (ISS) Manager
- Click the extended application (SharePoint –84 – FBA in this example).
- Double-click .Net Users
- In the Actions section click “Set Default Provider” and select the provider name you used in your web.config edits.
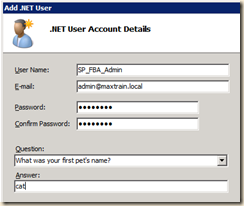
- In the Actions section click New and add a user! Add at least one user to serve as the Site Collection Owner. Add a few test accounts while you are at it.
Note that the password rules enforced here (length, strength) are defined in the membership provider in the web.config.
Fix up Central Administration
You now have an FBA application and a user, but no way to enter the user. Central Administration does not know about your membership provider, yet…
You need to duplicate the membership provider and connection string sections in Central Administration’s web.config file, but we are not going to make Central Admin an FBA application. Much of what you do here will be the same as the extended application.
- Open the web.config for Central Administration (The inetpub folder will probably be the port number of Central Admin)
- Add the connection string, membership provider and optional role provider sections:
<connectionStrings>
<addname="aspnetdb"
connectionString="Data Source=MAXSP2010Beta2\sharepoint;Initial Catalog=aspnetdb;Integrated Security=True"
providerName="System.Data.SqlClient" />
</connectionStrings>
<system.web>
<membershipdefaultProvider="MyAspNetSqlMembershipProvider">
<providers>
<clear/>
<add name="MyAspNetSqlMembershipProvider"
type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"
connectionStringName="aspnetdb"
enablePasswordRetrieval="false"
enablePasswordReset="true"
requiresQuestionAndAnswer="true"
applicationName="/" requiresUniqueEmail="false"
passwordFormat="Hashed" maxInvalidPasswordAttempts="5"
minRequiredPasswordLength="7" minRequiredNonalphanumericCharacters="1"
passwordAttemptWindow="10" passwordStrengthRegularExpression="" />
</providers>
</membership>
<roleManager enabled="true" defaultProvider="AspNetWindowsTokenRoleProvider">
<providers>
<add name="MyAspNetSqlRoleProvider" connectionStringName="aspnetdb"
applicationName="/"
type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a"
/>
</providers>
</roleManager>
- Now find this following line and copy and paste it using your membership provider’s name:
<add key="AspNetSqlMembershipProvider" value="%" />
- Now you should be able to use Central Administration to add an FBA user as a Site Collection Administrator:
- Go to Central Administration and click Application Management and then “Change site collection administrators”
- Add the FBA account, either as the Primary or Secondary.
Interesting footnotes…
- A new FBA user can only be added to the site from a logged on FBA user. A new Windows news can only be added by a logged in Windows user. Once a user had been added to a site from either side, the user can be added elsewhere (task lists, other permissions, etc) by users of either type.
- FBA authenticated admin/user click the Browse button on Assign To field in a task list and does a search… they can find all users in the FBA store and only Windows users how already have some type of access to the site.
- Windows authenticated admin/user click the Browse button on Assign To field in a task list and does a search… they can find all users in Windows/AD and only FBA users how already have some type of access to the site.
Other things you need to research…
- FBA (2007 and 2010) remote application access has interesting issues with / depends on Cookies so Office (and other application) integration (much better with Office 2007 SP2) may not work, or keep prompting users for credentials.
- SharePoint (still) does not include user administration tools: add user, edit user, change user password, etc. There is a codeplex.com project for 2007 that you can update for 2010.
Did I missing anything? Leave a comment!
.









13 comments:
great tutorial....
but this tutorial only valid if using window classic authentication...
can u show configuration for claim based authentication too?
Anonymous,
My purpose for this little article was that all of the other articles on the web covered Claims Based and not FBA. Google "sharepoint 2010 fba" and most of the articles are on Claims and FBA or Claims for FBA and LDAP, etc.
As an example see this one: http://blogs.msdn.com/sridhara/archive/2010/01/07/setting-up-fba-claims-in-sharepoint-2010-with-active-directory-membership-provider.aspx
Mike
This doesn't work for me. I followed your guide, but when I come the the part where I shall set the extended web app to use Forms authentication, everything falls apart. The 'Forms' option is grayed out :-(
Yes, I have xx-checked all config's!
Any ideas?
Helge,
The only thing that I can think of is that the membership entry in your web.config is not right. But I just tried a few things and could not get Forms to gray out. Let me know if you find the problem.
Mike
Have same issue as Helge, Forms radio button disabled when editing Authentication of extended web app. This is the RC build.
Many Thanks,
Brian
> This is the RC build
And that may explain why I can't duplicate it.
Post back here if you find a solution!
Mike
Nice tutorial,
but how exactly do I add the FBA users to the CA in the last step? FBA names are not getting resolved! Any ideas?
Anonymous,
The above steps worked in the Beta 2, but as others have indicated, it does not work with the RC. So, you need to use the Claims Based approach documented elsewhere.
Mike
Well I found the solution, I had to give the Application Pool user full access to the membership provider DB. After that it worked like a charm!
Thnx again
Hi,
I followed the steps listed here but got struck when i tried to modify the authentication from windows to form in "Edit Authentication" step. Only Windows option in radio button is enabled and rest (Forms and Web Single Signon) is grayed out. Could yo please tel me steps to solve this...
Thanks in advance
Saravanan Michael
Saravanan,
The article above only worked in the Beta 2 version. You will need to use the new Claims Based Authentication to support Forms Based Authentication.
Mike
you mentioned that there is a codeplex project to maintain users in 2007. Can you tell me where that is. I cant seem to find it.
russell,
The 2007 version:
http://fba.codeplex.com/
and the 2010 version:
http://fbamanagementtool.codeplex.com/
Mike
Post a Comment
Note to spammers...
Spammers, don't waste your time... all posts are moderated. If your comment includes unrelated links, is advertising, or just pure spam, it will never be seen.